Well have you?
Better Than Kevin Smith Masters of the Universe
Shut Yer Pi-Hole!
No seriously, get it shut.
Reading through Reddit the other day, I discovered a very cool piece of software called Pi-hole that acts as DNS for your home network to black hole all DNS requests for known advertiser and/or privacy-destroying domains.
I installed it last weekend on a Raspberry Pi I had laying around the house, made a few changes to my internal network (more on that later) and then hardwired the Pi to my router.
Annnnnnddddd…. We’re Back!
I had a HELLUVA time trying to get this space back up and running over the past four days. There might be some interest so I’ll describe some of the issues I ran into. My geek ego is damaged. Read on to discover why.
Zuckerberg And a Bold Faced Lie
Think it’s super important for people to watch this and think about how far we’ve come in 9 years. Watch and remember. Maybe it’s time to re-think how much you’re sharing on the “Social Network”.
Remember: if you’re not paying for a service, you’re the product. More after the video.
When Facebook opened to the public, as opposed to just Harvard students, I signed up almost immediately and thought it was neat. Here’s my first post from July 7, 2007:
How exactly should I feel about jumping on this fucking bandwagon? Ashamed? Oh, most assuredly.Engaged? No, I’ve coded a better web interface in my sleep. I awoke with a hard-on it was so good. Feeling a sense of security? Umm… no. Now any knob who once knew me, knew of me or simply knows my name can peer into whatever detail I choose to leave on this site. Retarded. Ummm yeah. I’m done. I’m on facebook. Yay.
Only slightly prophetic, no?
One day soon, I’m going to swap over all my “social networking” to this site where I have a bit more control. Oh, I hold no illusions; anyone that’s actually interested in my content on the Internet can download it and use it as they see fit but I have control over what I share with the world here instead of thinking I have some modicum of privacy. The illusion that most social networking enthusiasts work under is that they have privacy. Seeing my FB data dump shows me how much I’ve shared over eleven years and that’s making me move more here, under my control.
I think more people should look to control the content that’s about them floating around on the net. Maybe I’m starting to get a bit paranoid but I want my thoughts, pictures, status updates to be mine and not sold to a company that will attempt to make money from me without me getting equal value in return.
I Had a Feeling
Just watch this. It’s worth the 3 minutes of your time to put some emotion into your day.
Game of Thrones Intro: 80’s Style
Password Security: Get Your Shit Together, Zaal
So I got an interesting email from Google this evening:
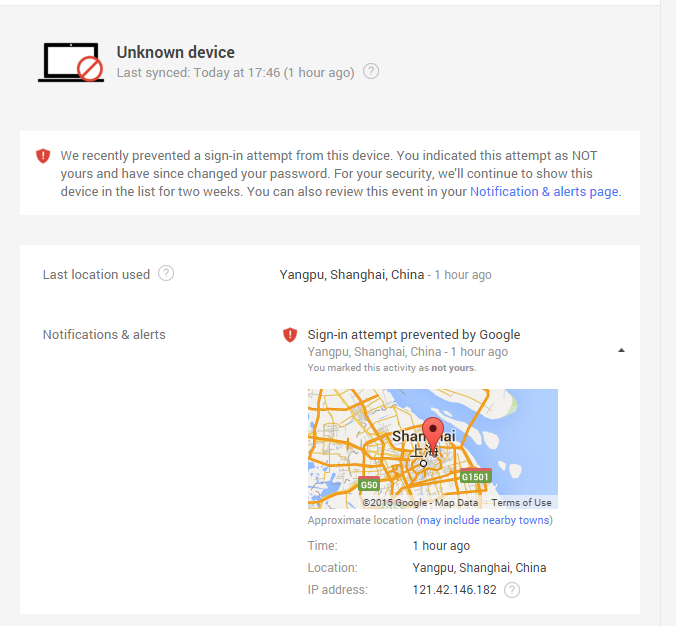
The attacker had my password and my gmail account name. The only reason they didn’t get into my account, I think, is because I use two-factor authentication that requires me to input a randomly generated number from the Google authentication app that resides on my phone before it will complete the authentication process and allow full access.
The worrying thing for me was wondering how my password was compromised. I actually put some brain cells behind the process and realized I gotten incredibly lazy in my choice of password since I’d activated two factor. My password was 8 characters consisting of 6 alphas and 2 numbers and three different permutations that I rotate through over the course of a year. I’ve since changed that password, and any others that used such a simple algo and changed it to something I use on other sites which consists of four words that mean absolutely nothing when put together, equal 25 characters in length and are easily remembered.
Still concerned, I visited BreachAlarm.com and discovered that there was a data breach at Xsplit.com back in 2013 and some of that data was only brought to light on the 25th of October of this year. No coincidence that a month later, my email account is being prodded with the hope of taking it over.
The cool thing about most web-based accounts these days (I’ll add that this is in my experience) allow for the main email attached to an account will be notified in the event of a change in account information. Because of this, the attacker really wants to take over the contact email account so they can control the information reaching the target before the attacker’s actions have reached completion.
So I’ll just put this one here, again, for the use of people who may be of the mind that your password needs to be hard to remember. Your password doesn’t need to be complex; just needs to be difficult to guess.

